Firmware Vulnerability Management using NCM
Firmware vulnerabilities can lead to critical security issues that could put your networks at risk. However, Site24x7's Network Configuration Manager (NCM) helps you identify firmware vulnerabilities proactively and take corrective action, like upgrading your firmware, before any threats occur.
How it works
Site24x7's Network Configuration Manager scans your network for firmware vulnerabilities and identifies risks based on vulnerability data provided by National Institute of Standards and Technology (NIST) vulnerability management. The Firmware Vulnerabilities Dashboard displays the firmware versions, the number of exposed devices, and the list of vulnerabilities. You can click on any vulnerability to check if a patch is available and check the reference links displayed on the screen to understand how to protect your device against the vulnerability. This minimizes vulnerabilities in your network devices and safeguards them against possible exploits.
Here's a video to help you get started:
Categorizing firmware vulnerabilities
NCM categorizes firmware vulnerabilities into four categories: Critical, Important, Moderate, and Low. The severity of the vulnerabilities is calculated based on the Base Score.
The Base Score is calculated based on the following metrics:
- Exploitability Metrics: The ease of exploiting the vulnerability, comprising of components such as Attack, Complexity, and Authentication.
- Impact Metrics: The impact of the vulnerability on your organization, comprising of elements like Confidentiality, Integrity, and Availability.
The score categorization is as follows:
| Base score | Severity |
| 9.0 - 10.0 | Critical |
| 7.0 - 8.9 | Important |
| 4.0 - 6.9 | Moderate |
| 0 - 3.9 | Low |
Supported devices
At present, Network Configuration Manager supports firmware vulnerability management for devices from the following vendors:
- Citrix
- MikroTik
- Check Point
- F5
- Blue Coat
- Infoblox
- Riverbed
- Huawei
- NETGEAR
- HPE
- NetScreen
- Cisco
- Juniper
- Palo Alto
- HP
- Aruba
- Arista
- Fortinet
- Dell
Viewing vulnerabilities for each device
To view firmware vulnerabilities in your network:
- Log in to your Site24x7 account.
- Navigate to Network > NCM and click the device for which you wish to view the firmware vulnerabilities.
- Click the Vulnerabilities tab to view the relevant details such as: common vulnerabilities and exposures ID number (CVE ID), Base Score, CVE Type, Severity, State, and Discovered Time.
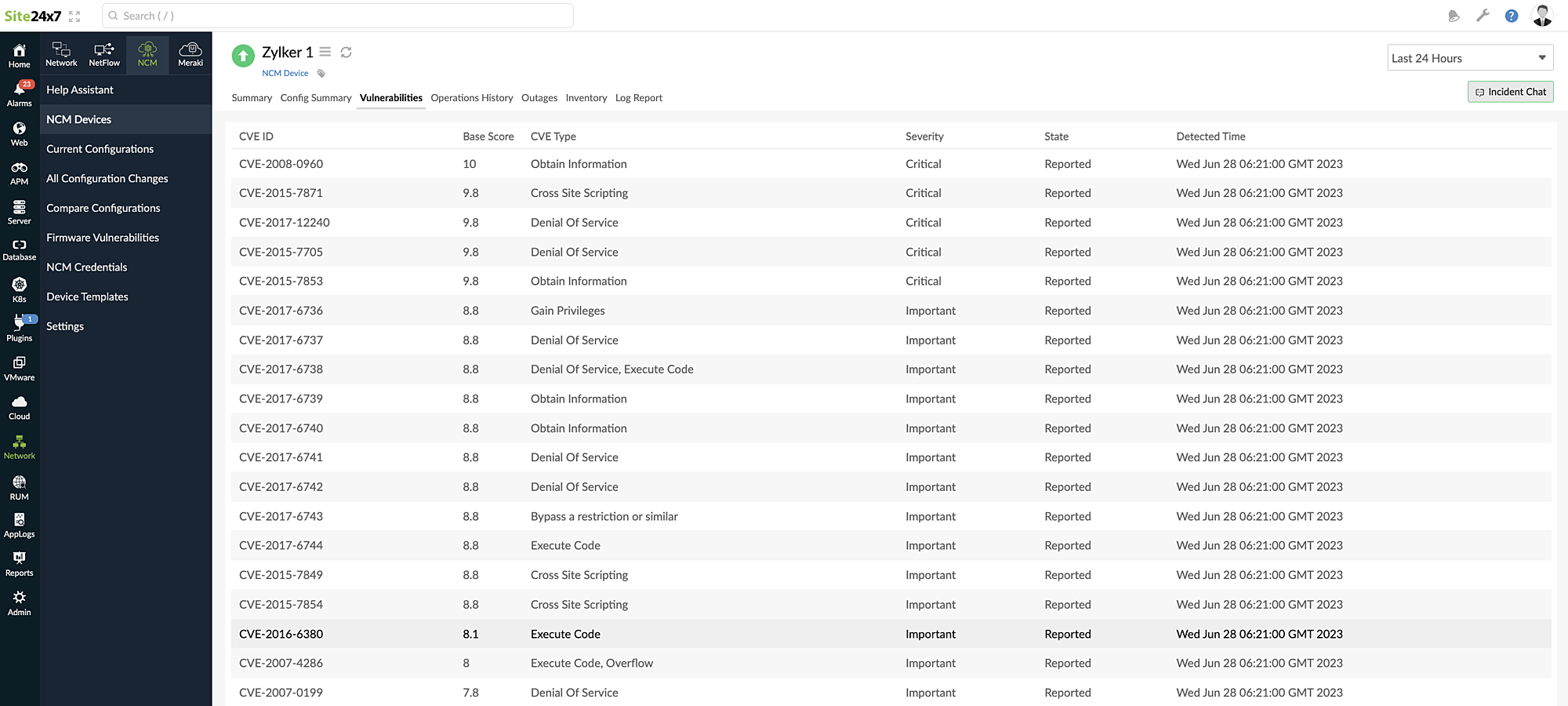
Figure 1. Viewing firmware vulnerabilities. - Click each record to view details about each vulnerability in that device.
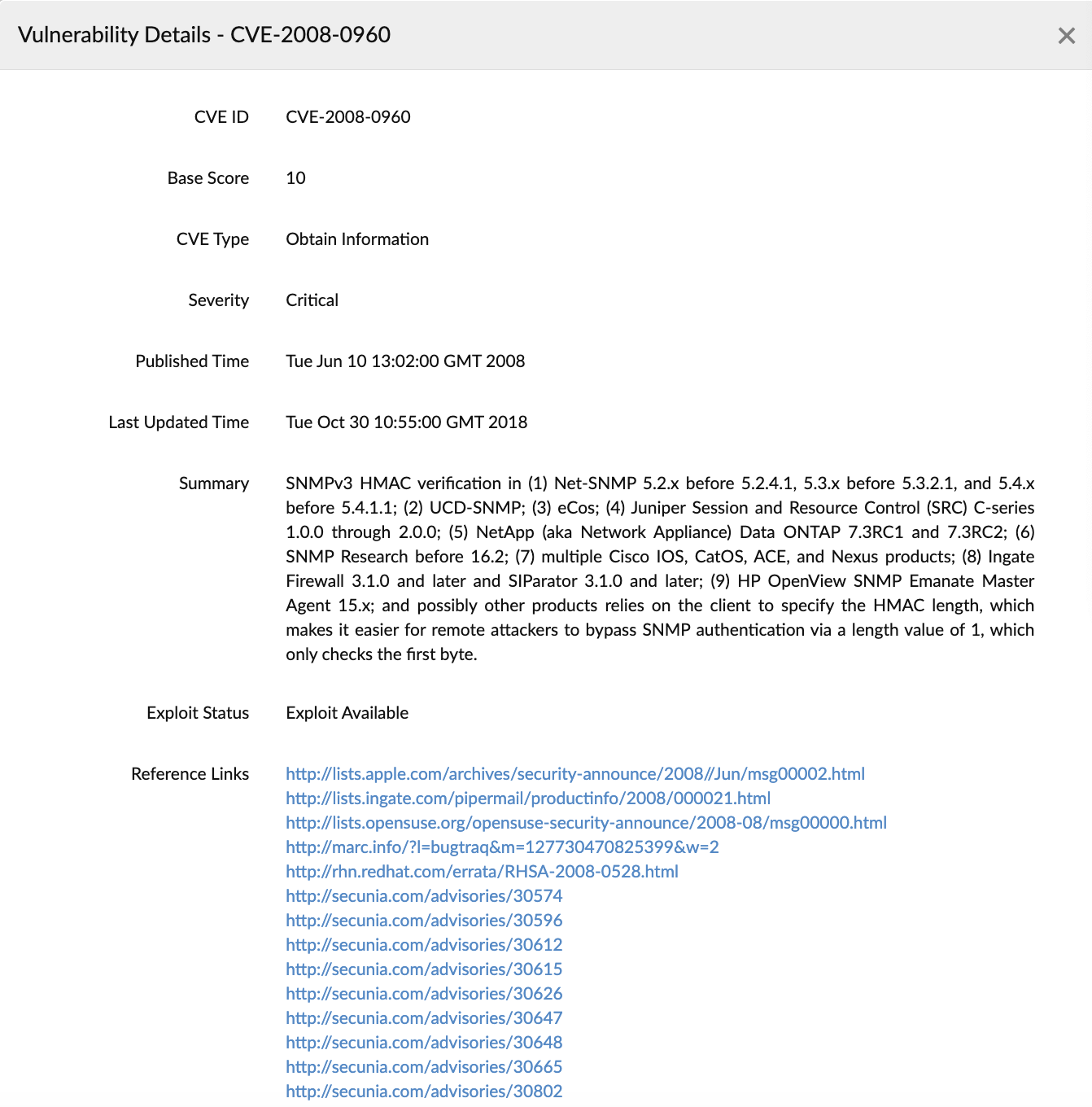
Figure 2. Vulnerability details. - Navigate to the Inventory tab to add or modify the threshold criteria for new vulnerabilities.
Firmware Vulnerabilities Dashboard
- Navigate to Network > NCM > Firmware Vulnerabilities to view the vulnerability details for all the monitors that you've added in Network Configuration Manager.
- Vulnerabilities: Here, you will be able to view all CVE IDs and vulnerabilities in your network devices according to data provided by NIST vulnerability management. Click Critical, Important, Moderate, or Low to view vulnerabilities under each category.
- Search vulnerabilities according to CVE ID, CVE Type, Severity, Exploit Status, or Description for faster access to a record.
- Select each record to view additional details about each vulnerability, e.g., which device is affected.
- Click View Details to view detailed information about each vulnerability record as shown in Fig. 2.
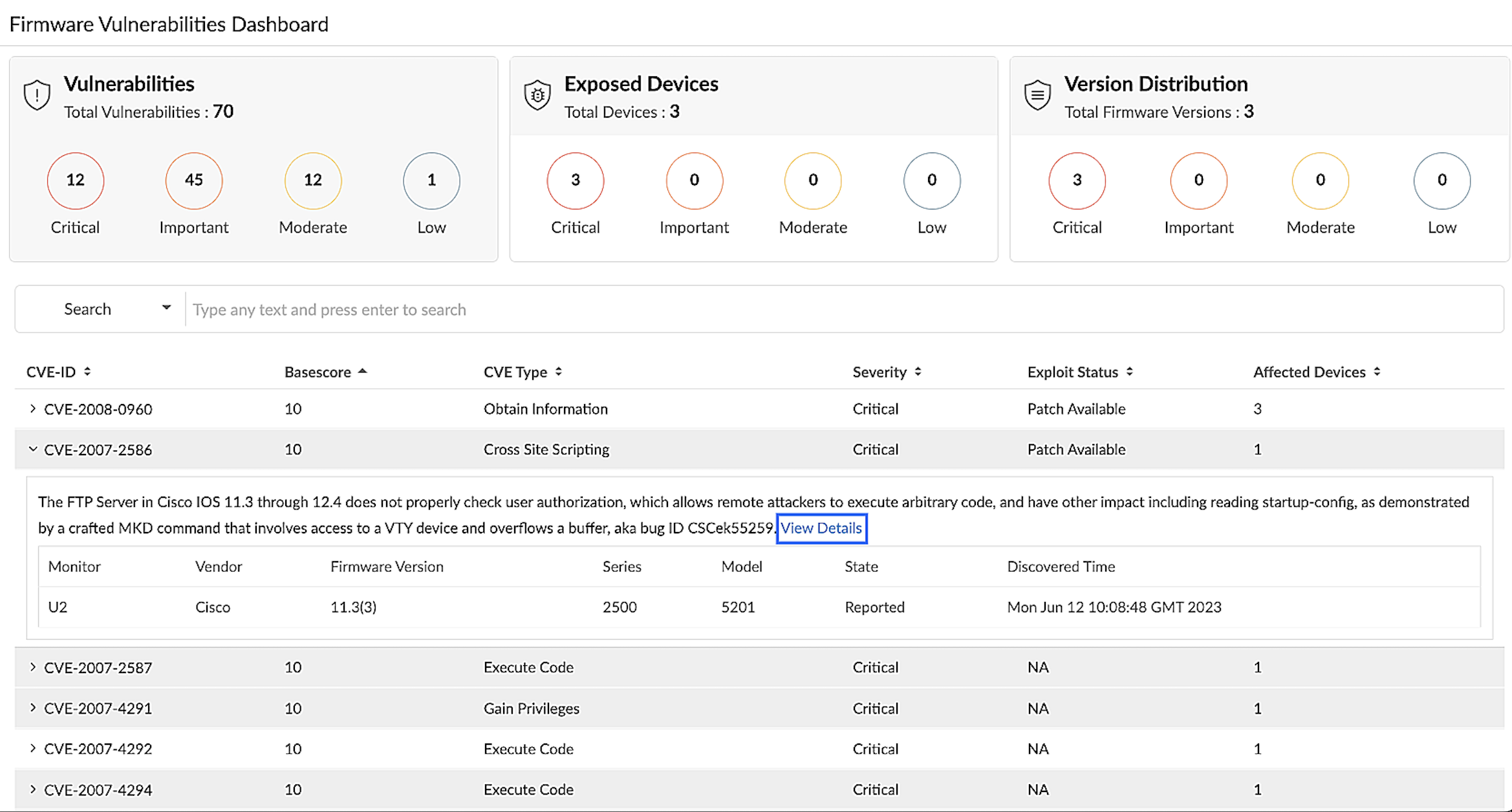
Figure 3. Firmware Vulnerabilities Dashboard - Total Vulnerabilities.
- Exposed Devices: Select Exposed Devices to view all the devices that are exposed to firmware vulnerabilities. Click Critical, Important, Moderate, or Low to view devices under each category.
- Search devices according to Monitor Name, Vendor, Firmware Version, Series, or Model for faster access to a record.
- Select each record to view the list of vulnerabilities in that device. The total vulnerabilities in each device is available under Vulnerabilities Count.
- Click the CVE ID to view detailed information about each vulnerability record as shown in Fig. 2.
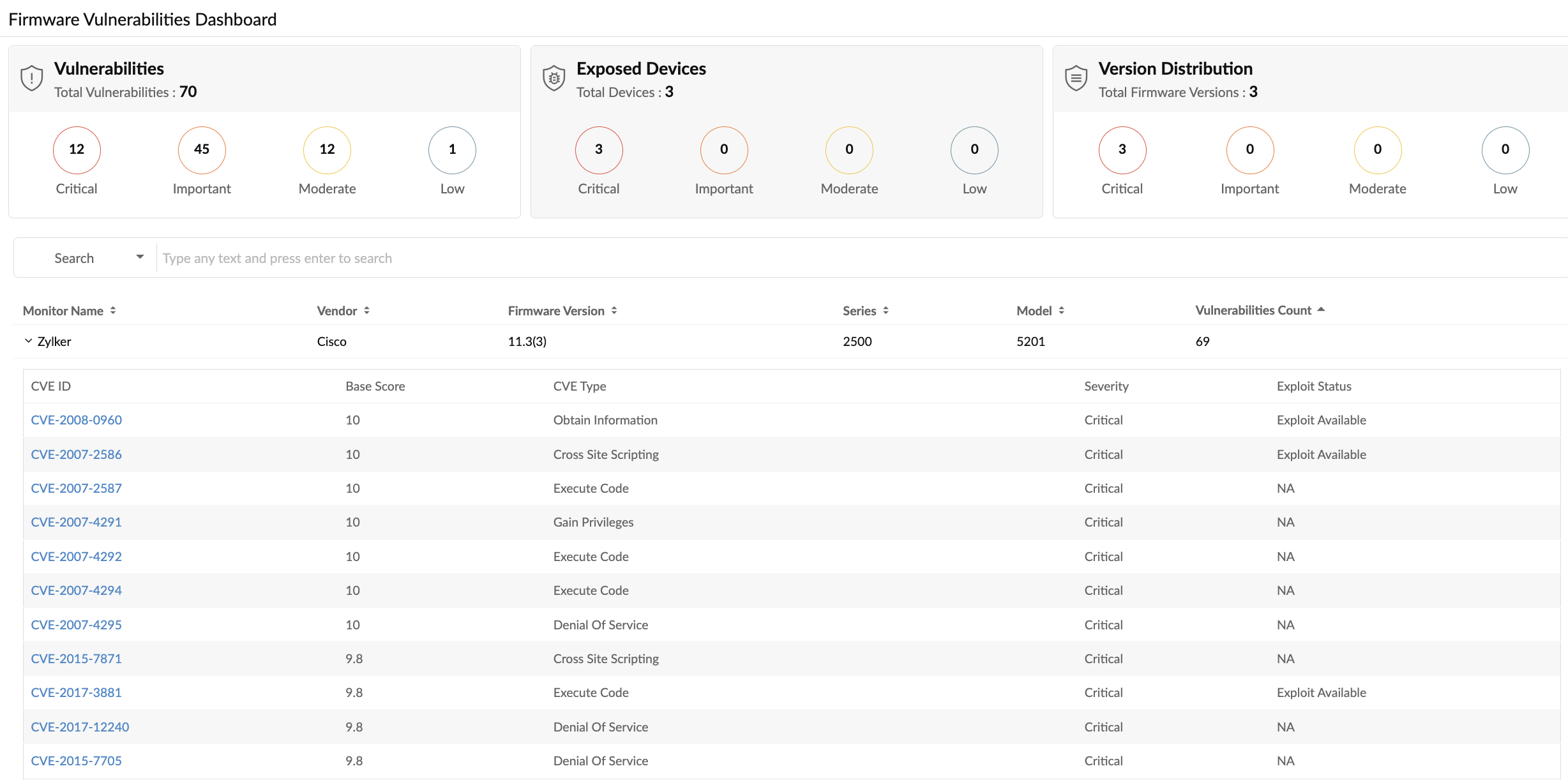
Figure 4. Firmware Vulnerabilities Dashboard - Exposed Devices.
- Version Distribution: Select Version Distribution to view the versions that have active vulnerabilities. Click Critical, Important, Moderate, or Low to view devices under each category.
- Search devices according to Vendor or Firmware Version.
- Select each record to view the list of vulnerabilities in devices by that vendor. The total vulnerabilities in each device is available under Vulnerabilities Count.
- Click the CVE ID to view detailed information about each vulnerability record as shown in Fig. 2.