by Subashree K
Greetings!
We are glad to announce that Site24x7 AppLogs now supports Azure NSG flow logs. Gain unparalleled visibility into Azure network security groups (NSG) traffic and activity with AppLogs.
Azure NSG controls inbound and outbound traffic to and from Azure resources. Flow logs capture information about IP traffic, such as source and destination IP addresses, source and destination ports, protocol, and whether the traffic was allowed or denied.
By integrating NSG flow logs with Site24x7, you can take control of your Azure network infrastructure, allowing for centralized monitoring, optimizing performance, enhancing security, and ensuring compliance. You will also receive alerts on key metrics, with events reported in real time, enabling you to detect any issues or security concerns quickly.
You can follow the steps mentioned in this document to configure NSG flow logs in AppLogs.
AppLogs provides an exclusive dashboard that gives you the ability to monitor and analyze multiple elements of traffic.
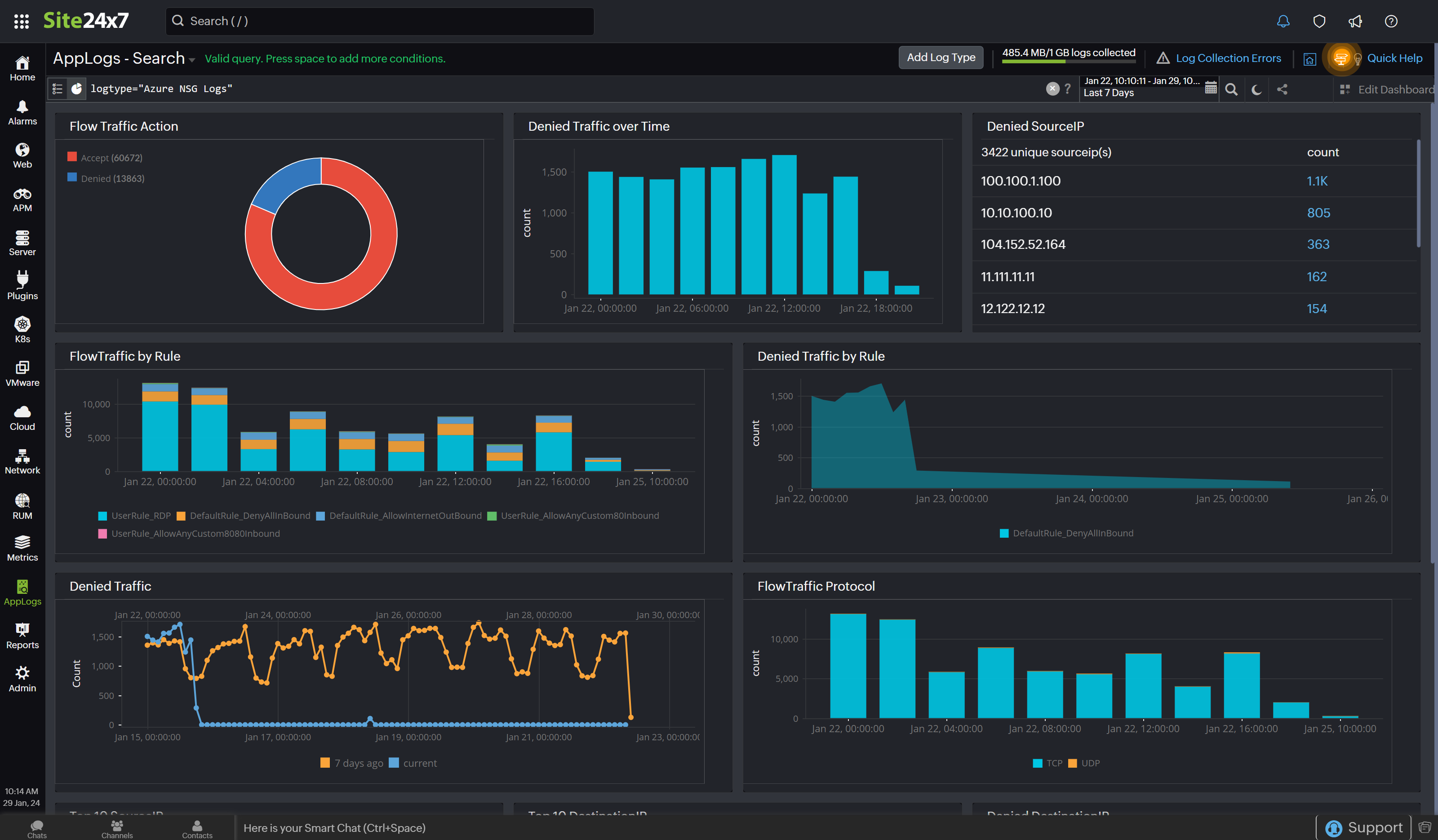
Elements of this dashboard include:
- Flow Traffic Action: Visualizes the actions performed on network traffic, differentiating between allowed and denied flow actions for enhanced security insights.
- Denied Traffic Over Time: Visualizes the patterns of denied network traffic, identifying trends for proactive monitoring and response.
- Denied Source IP: Identifies the specific source IP addresses associated with denied network traffic, facilitating the investigation and mitigation of potential security threats.
- Flow Traffic by Rule: Analyzes different rules impacting the flow of traffic within your Azure environment.
- Denied Traffic by Rule: Analyzes the denied network traffic, facilitating targeted analysis to identify rule-specific issues.
- Denied Traffic: Monitors and analyzes denied network traffic, providing crucial information for identifying potential security threats.
- Flow Traffic Protocol: Analyzes the network traffic based on protocol, identifying the communication patterns involved in the data flow within your Azure environment.
- Top 10 Source IP: Identifies the ten source IP addresses with the highest traffic volume, offering crucial insights into network activity.
- Top 10 Destination IP: Identifies the ten destination IP addresses with the highest traffic volume, offering crucial insights into network activity.
- Denied Destination IP: Identifies the destination IP addresses associated with denied traffic, providing visibility into potential security threats.
- Top 10 Destination Port: Identifies the ten destination ports with the highest traffic, providing insights that can be leveraged for strategic network optimization and security enhancements.
- Traffic Destination: Identifies the inbound and outbound traffic destinations, providing a comprehensive view of communication endpoints.
Stay on top of your network activity and make informed decisions with AppLogs. Feel free to drop your feedback, suggestions, and feature requests as comments below.
Until next time,
Happy logging!
Like (1)
Reply
Replies (0)