Securing your digital fort: Why firmware vulnerability management is essential

Think of your network device firmware as a fortress that can withstand attacks and protect you from potential threats in the digital world. It acts as a guardian, keeping hackers and malicious software at bay so you can be confident that your data is safe.
However, any imposing medieval fortress standing tall and proud with seemingly impenetrable walls, no matter how strong it seems, can't keep up with a relentless barrage from the latest weaponry. Without reinforcements, it's only a matter of time before the fortress succumbs.
Similarly, imagine device firmware that has not been updated for a while but seems secure and protected. Still, it cannot keep up with the latest threats and vulnerabilities that constantly emerge. It becomes a pathway for threat actors to exploit and gain access to sensitive information. So, just like a fortress needs constant reinforcement to withstand new threats, device firmware also needs regular updates to keep up with the ever-changing security landscape.
Keeping up with firmware updates on all network devices can be a daunting task for network admins. With so many devices to manage, it's easy to overlook a firmware update. The solution? Implementing a firmware vulnerability management tool that helps ensure that all devices in your network are up to date and secure.
What is firmware vulnerability management?
Software embedded in your hardware devices, known as firmware, can be vulnerable to attacks. Vulnerabilities in the firmware's code can be exploited by attackers to compromise network security, cause device malfunctions, and lead to privacy breaches. Outdated firmware, emerging threats, faulty software, incorrect updates, or human errors are some of the reasons why these vulnerabilities occur.
But, worry not! Firmware vulnerability management is your knight in shining armor, constantly on the lookout for security gaps in your network devices. It scans backed-up device configurations to determine if your firmware version has any vulnerabilities that need attention or patch fixes from the vendor.
Why do you need firmware vulnerability management?
Every software contains bugs, so it's no big deal if there are bugs in the device software, right? Wrong. Let's see how these bugs can affect your network and the worst that can happen.
As technology advances, so do the methods that hackers use to infiltrate your networks. These cybercriminals are always on the lookout for vulnerabilities that they can exploit to gain access to your confidential information. Once they breach your system, they can wreak havoc by introducing viruses, stealing the personal information of your clients, and even remotely manipulating your devices without detection.
The consequences of a successful breach can be extremely severe. Not only can it lead to frequent system failures and downtime, but it can also result in significant financial loss. And when information about the breach becomes public, it can have a lasting impact on the trust that your clients have in you.
That's why it's crucial to stay vigilant and take all necessary measures to safeguard your networks against hackers. By doing so, you can protect your business and your clients from the devastating effects of a cyberattack.
What can you do if there is a firmware vulnerability?
- Assess the severity of the vulnerability by using your firmware vulnerability management tool.
- Check if there are any available patches to fix the issue.
- If patches are available, visit the device vendor's page to understand how to apply them.
- In case patches are not available, get in touch with the device vendor to understand the next course of action.
How can Site24x7 help?
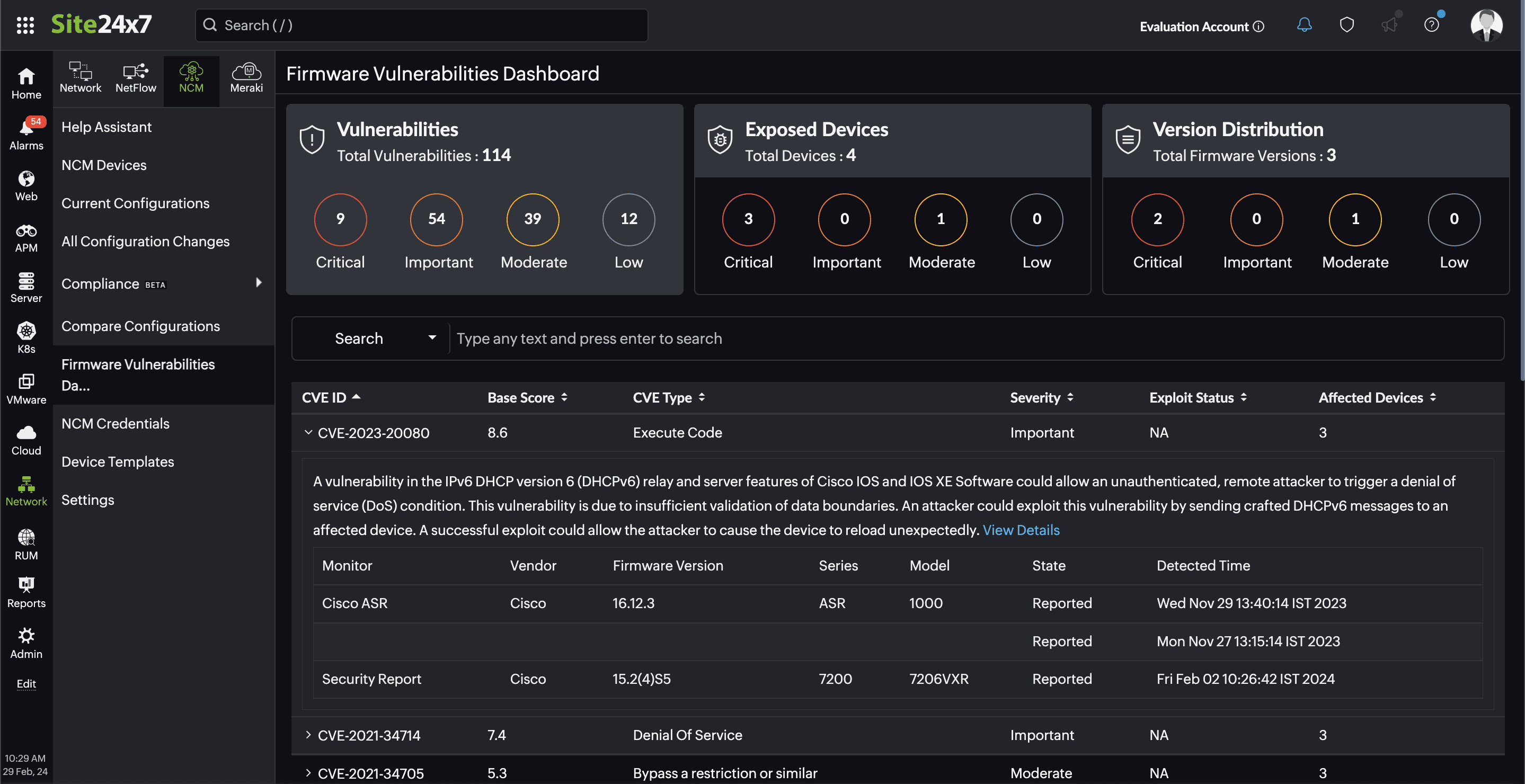
Tracking firmware vulnerabilities is like finding a needle in a haystack, only more tedious. That's why it's crucial to switch to an automated firmware vulnerability management tool like Site24x7, which offers firmware vulnerability management as part of its network configuration manager.
Our comprehensive network configuration management (NCM) tool helps you effortlessly track both device configuration changes and firmware vulnerabilities in a single window. Whenever there's a change in the device configuration, our NCM tool makes backups. It also checks the firmware version against data from the National Institute of Standards and Technology (NIST). If the NIST has documented a vulnerability, then the NCM tool will display the relevant data on a firmware vulnerability dashboard. And that's not all—it even categorizes vulnerabilities based on their severity and provides relevant links to any patches available.
And guess what? With Site24x7, you can even monitor your device's health, performance, and traffic details. If you're uncertain about how this solution will work for your organization, you can take advantage of our 30-day, free trial and experience the difference for yourself.
Comments (0)