A network configuration manager is a tool that helps in the structured processes of governing, tracking, validating, and maintaining the configuration state of network devices, including routers, switches, firewalls, wireless controllers, load balancers, and edge appliances. As networks expand across data centers, branches, WAN edges, and cloud environments, configuration consistency has a direct impact on availability, performance, and security.
A robust network configuration manager ensures that every configuration change is captured, versioned, analyzed, and compliant with operational and security standards. It mitigates risks caused by unauthorized edits, eliminates configuration drift, accelerates restoration during failures, and provides an auditable change history for security and compliance teams. With a centralized, automated approach, network configuration management (NCM) becomes a foundational layer for predictable, secure, scalable network operations.
Operational risks of manual NCM
Today, networks face architectural complexity, rapid change cycles, and increasing security requirements. Without structured configuration management, IT teams face:
1. Configuration drift across a multi-vendor device environment
Manual updates introduce inconsistencies that lead to routing failures, ACL mismatches, VLAN misalignment, and performance issues.
2. Limited visibility into configuration changes
Teams lack insight into who made a change, when it occurred, and how it impacted downstream network performance.
3. The risk of outages from manual errors
A single incorrect command—an ACL line, OSPF metric, or VLAN instruction—can disrupt critical services.
4. Incomplete change governance
Without approvals, RBAC, or audit logs, teams face compliance violations and operational blind spots.
5. Firmware vulnerabilities and outdated OS versions
Unpatched firmware exposes devices to CVEs, exploits, and lateral movement risks.
6. Time-consuming manual provisioning and updates
Scaling, patching, and credential rotation across distributed networks become operationally expensive.
7. Difficulty maintaining compliance
Policies related to passwords, SNMP settings, banners, SSH parameters, and access rules must be consistently applied across devices.
Benefits of automated NCM
Automated NCM helps overcome these challenges through:
1. Improved reliability
Version control and automated backups reduce the impacts of unauthorized changes or failed updates.
2. Faster recovery
One-click rollback enables teams to restore stable configurations immediately during outages.
3. A stronger security posture
Firmware insights and compliance checks highlight vulnerabilities and violations before attackers can exploit them.
4. Operational consistency
Templates and automation workflows ensure uniform configuration across devices and locations.
5. Reduced manual effort
Bulk updates and automation eliminate repetitive CLI work.
6. Full change accountability
RBAC and audit logs provide traceability for all modifications.
7. Lower operational costs
Automation, cloud delivery, and centralized visibility reduce administrative overhead.
Understanding how NCM works
An NCM solution delivers value through a structured, repeatable, end-to-end workflow that governs the entire life cycle of a network device’s configuration.
1. Device discovery and inventory creation
The platform identifies devices across the network, collects initial configurations, and builds a structured inventory containing the following information:
- Device roles and models
- OS and firmware versions
- Hardware details
2. Automated configuration retrieval and backups
Periodic and event-triggered retrieval of running and startup configurations ensures that the latest version is always stored.
3. Version control and difference analysis
Every change creates a version snapshot. Engineers can:
- Compare versions line by line.
- Identify drift.
- Detect unauthorized or error-prone edits.
4. Compliance validation and policy checks
Configurations are scanned against:
- Internal security baselines.
- Operational standards.
- Industry frameworks.
Violations trigger alerts and recommended fixes.
5. Change governance and RBAC enforcement
Users are assigned roles with specific permissions. Approval workflows ensure that critical changes pass review before deployment.
6. Configuration automation and templates
Predefined templates or CLI snippets (configlets) can be applied to:
- Update SNMP.
- Modify ACLs.
- Rotate credentials.
- Push routing changes.
- Apply VLAN updates.
- Enforce security banners.
Bulk execution enables rapid, consistent deployment.
7. Firmware visibility and vulnerability mapping
The system detects firmware versions and correlates them with known vulnerabilities (CVEs), enabling patch planning.
8. Continuous monitoring and correlation
The solution analyzes performance anomalies alongside configuration changes to help teams identify root causes and prevent repeat incidents.
Key components of NCM
Maintain complete device visibility with configuration discovery and inventory management
A reliable system identifies all managed devices, collects their initial configurations, and maintains an up-to-date inventory of device types, models, OS versions, and logical attributes.
Prevent downtime with automated configuration backups
Every configuration change triggers an automatic backup of the running and startup configurations. Teams maintain instant access to previous versions for auditing, analysis, and recovery workflows.
Detect misconfigurations with version control and difference analysis
Versioning enables engineers to compare any two configurations line by line, identify drift, detect unauthorized changes, and quickly isolate misconfigurations.
Ensure compliance with policy enforcement and automated checks
An NCM platform uses rules to evaluate configurations against internal standards (password rules, SNMP policies, and ACL structures) and regulatory frameworks, providing violation summaries and remediation options.
Accelerate operations with configuration automation
Template-driven updates and bulk automation workflows help teams push standard configurations, distribute changes, rotate credentials, update SNMP strings, and apply ACL or routing changes across multiple devices.
Strengthen security with firmware visibility and vulnerability insights
Mapping firmware versions against known vulnerabilities (CVEs) strengthens the network's security posture and supports planned, controlled upgrade cycles.
Control access and audit all changes with RBAC
Role-based access, change approvals, and a comprehensive audit trail help ensure that all modifications adhere to organizational governance policies.
Correlate changes with performance using monitoring integrations
Configuration changes are correlated with performance degradation, interface errors, CPU and memory anomalies, and security events for end-to-end operational visibility.
Use cases: How Site24x7 helps
Eliminate configuration drift
- Scenario: A large enterprise experiences intermittent routing issues across multiple branches. The investigation reveals inconsistent OSPF configurations between devices.
- Outcome with Site24x7: Automated backups, scheduled compliance checks, and drift detection identify the inconsistent statements. A standardized configuration template is pushed across all routers, restoring stability.
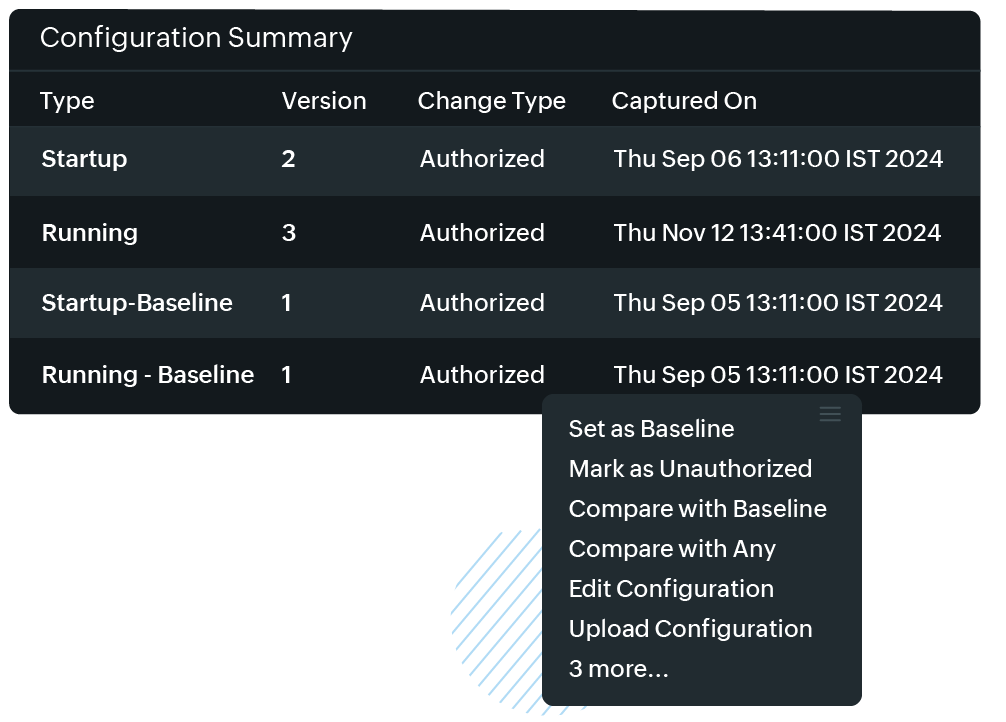
Enable safe multi-team collaboration with draft uploads
- Scenario: The network engineering team prepares a major redesign of the QoS policy. The architecture and security teams must review draft configurations before deployment.
- Outcome with Site24x7: Draft uploads, version comparisons, and approval workflows enable controlled peer review without requiring access to production devices. Once approved, changes are deployed at scale using automation.
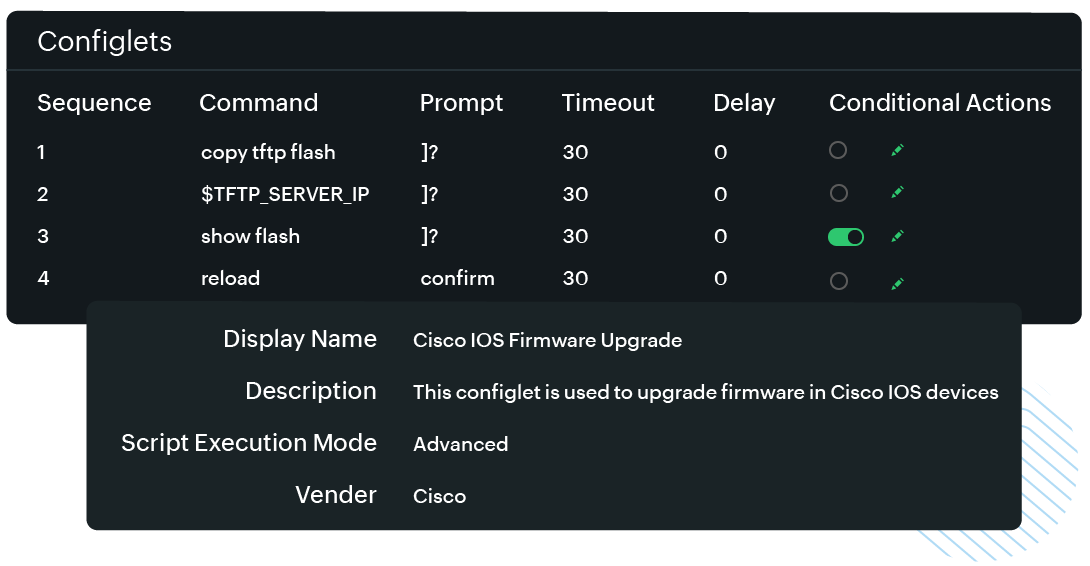
Accelerate operations with zero-touch bulk updates
- Scenario: Hundreds of switches require SNMP configuration updates due to a credential rotation policy.
- Outcome with Site24x7: A single automation workflow updates all affected devices, verifies execution success, and ensures a consistent configuration state across locations—without manual CLI intervention.
Reduce security risk exposure with firmware vulnerability management
- Scenario: The security team identifies a high-severity CVE affecting a specific router OS version. The team lacks visibility into which devices are impacted.
- Outcome with Site24x7: Firmware inventory data instantly reveals all the affected devices. Teams plan staggered upgrades and automatically validate the post-upgrade configuration and compliance.

Enforce baseline security policies with compliance checks
- Scenario: An internal audit reveals weak password settings and outdated banner messages across network devices.
- Outcome with Site24x7: Automated compliance checks highlight violations, provide remediation lines, and validate corrections after enforcement templates are pushed.

Achieve full operational control with NCM
- Scenario: A configuration change to firewall ACLs impacts
application access across regions.
- Configuration drift is detected.
- Difference analysis pinpoints the exact unauthorized change.
- A rollback restores the last known good version.
- Compliance checks validate policy alignment.
- Automated workflows push updated ACL templates to all users globally.
- Monitoring correlates with improved network performance post-remediation.
- Outcome with Site24x7: A complete closed-loop operation—detection, diagnosis, correction, and validation—is executed through a single platform.
Reinvent NCM in a SaaS-based environment
Operating modern networks requires deterministic control, consistent configuration enforcement, and continuous validation across distributed, multi-vendor environments. SaaS-based NCM software provides this operational framework by centralizing configuration states, enforcing policies, and automating device actions at scale.
Site24x7 unifies configuration versioning, automated backups, difference intelligence, compliance evaluation, firmware vulnerability insights, and more on a single cloud platform. Every change is tracked, validated, and tied to the network's performance and security posture. This eliminates configuration drift, shortens recovery times, and helps ensure predictable, governed operations.
By shifting configuration governance to the cloud, teams can remove on-premises infrastructure overhead, maintain continuous compliance, and apply baseline configurations and remediation logic consistently across devices. Site24x7 enables a controlled, data-driven operational model built on real-time visibility, policy enforcement, and scalable automation, establishing a resilient, future-ready network foundation.