What NSM is and why it matters
NSM is the practice of continuously observing network activity to detect suspicious behavior, policy violations, firmware vulnerabilities, and potential intrusions. It is a proactive approach to cybersecurity that relies on real-time traffic analysis, configuration management, and compliance tracking to protect your infrastructure.
Think of it as watching what is happening on your network and why. NSM helps you catch early indicators of threats, like:
Lateral movement across networks
Unauthorized configuration changes
Firmware-level vulnerabilities
Non-compliance
Traffic anomalies and data exfiltration attempts
Key features of our NSM tool
Site24x7 offers a unified, cloud-native platform packed with security-focused capabilities. Here's how it helps secure your network from every angle:
Network configuration management (NCM)
Automatically back up device configurations, track changes, and restore known-good versions when needed.
Compliance management and audit trail
Enforce policy-based rules and maintain an audit trail to meet internal and regulatory compliance needs.
Firmware vulnerability management and alerts
Detect outdated or insecure firmware across devices from major vendors like Cisco, Juniper, and more.
Network automation features
Streamline device management with scheduled backups, rule-based scripts, and automated responses.
Script execution for custom workflows
Execute scripts across routers, switches, and firewalls to automate remediation or collect diagnostics.
Centralized dashboard and alerting system
Stay on top of all your devices, traffic patterns, and alerts in one easy-to-use interface.
Traffic analysis with flow protocols
Gain visibility into network traffic usage and threats by tracking flows like NetFlow, J-Flow, sFlow, IPFIX, NetStream, AppFlow, and CFlow.

Automatically back up device configurations, track changes, and restore known-good versions when needed.
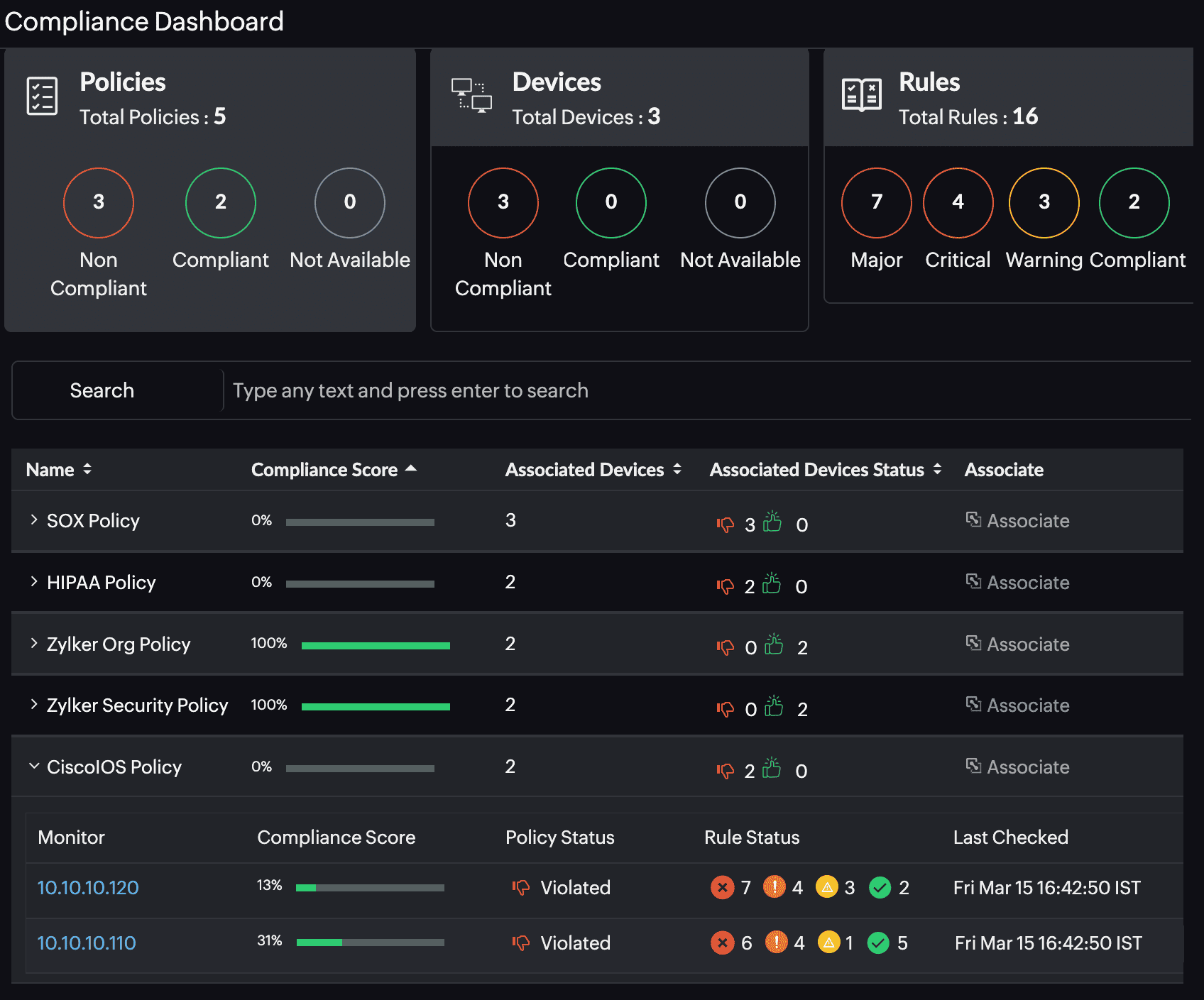
Automatically back up device configurations, track changes, and restore known-good versions when needed.
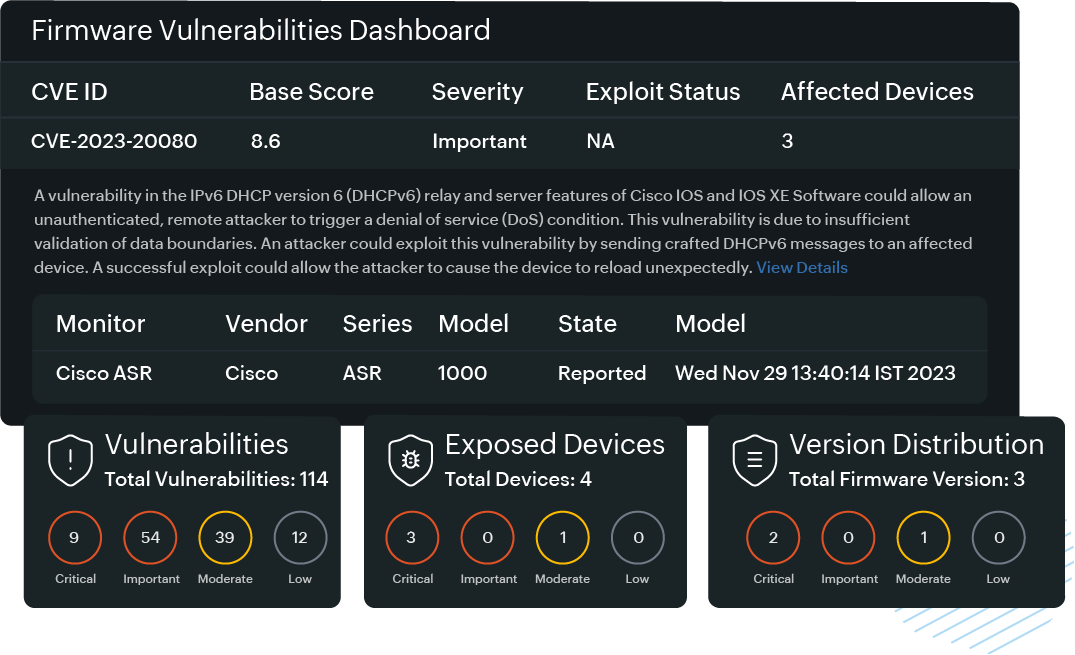
Detect outdated or insecure firmware across devices from major vendors like Cisco, Juniper, and more.

Streamline device management with scheduled backups, rule-based scripts, and automated responses.

Execute scripts across routers, switches, and firewalls to automate remediation or collect diagnostics.

Stay on top of all your devices, traffic patterns, and alerts in one easy-to-use interface.
Gain visibility into network traffic usage and threats by tracking flows like NetFlow, J-Flow, sFlow, IPFIX, NetStream, AppFlow, and CFlow.
AI for network security and monitoring
Artificial intelligence (AI) is changing how teams handle network security.
With Site24x7, AI and machine learning work quietly in the background to help you:
- Anticipate delays in response time or packet loss, which you can try to fix before it occurs.
- Learn typical behavior patterns to reduce noise and alert fatigue.
This is especially useful for large or distributed networks where human monitoring alone isn't enough. AI adds that extra layer of intelligence so you can focus on the threats that actually matter.
Why is Site24x7 the leading tool for network security monitoring?
There are a lot of NSM tools out there, but Site24x7 stands out for a few key reasons:
Cloud-native
No installations, no hassle. Monitor and secure your network from anywhere.
Unified
Get everything you need for security monitoring in one console.
Built for scale
From small IT teams to global enterprises and MSPs, Site24x7 adapts to your needs.
Integrates easily
Site24x7 supports integration with several third-party tools for deeper context and response.
Network security monitoring best practices
Want to make the most of your NSM setup? Here are some best practices to follow—most of which Site24x7 helps automate:
- Set baselines for normal network behavior to detect anomalies faster
- Use NCM to track configuration drift and prevent unauthorized changes
- Enforce compliance with automated rules and scheduled audits
- Patch firmware and flag vulnerabilities before attackers find them
- Use scripted responses to handle incidents quickly and consistently
- Fine-tune alerts so your team isn't drowning in notifications
Security isn't just about having tools—it's about using them wisely and consistently.
Get started with Site24x7's NSM
Ready to take control of your network security? Site24x7 makes it easy to get started:
Simple, agentless setup
Plans tailored for IT teams, enterprises, and MSPs
Free trial available—no credit card required
Extensive documentation and 24/7 support to help you at every step
Overview of network security monitoring
How does it help with compliance and auditing?
Site24x7 enables you to maintain a secure and compliant network environment through continuous configuration tracking, policy enforcement, and detailed audit trails. It logs every configuration change, alerts you to unauthorized modifications, and provides compliance reports that help during internal and external audits. This ensures that device configurations remain aligned with security and regulatory requirements.
How does NSM deal with encrypted traffic? Can it inspect TLS / SSL flows?
Site24x7 analyzes flow-level data to deliver visibility into encrypted traffic without decrypting payloads. It monitors connection metadata—like source, destination, protocol, and traffic volume—to help detect anomalies or suspicious communication patterns in encrypted sessions, all without compromising data privacy.
How are alerts prioritized or scored?
Alerts in Site24x7 are generated based on predefined thresholds and severity levels. You can customize alert conditions to reflect the criticality of specific devices or configurations. This allows critical policy violations and configuration drifts to be flagged immediately, while lower-priority issues are grouped for later review, ensuring efficient incident triage and response.
What is the performance overhead? Does this slow down the network or devices?
Site24x7 is designed to operate with minimal overhead. Since most monitoring functions are agentless and rely on flow exports or SNMP polling, device performance remains largely unaffected. Proper configuration of polling intervals and flow export rates ensures that monitoring doesn’t consume excessive bandwidth or resources on network devices.
Do I need to install agents or probes on my devices?
Site24x7’s network security monitoring is agentless for network devices. It collects data using existing network protocols such as SNMP and flow technologies, so there’s no need to deploy additional agents or probes on individual routers, switches, or firewalls. It uses the On-Premise Poller for secure data collection behind your firewall.
Ready to take the first step towards a secure network?
Try Site24x7 today and experience how effortless network security monitoring can be